Almost every profession and job requires that you understand how to use industry-specific tools, often referred to as ‘tools of the trade’, and this couldn’t be more true than for Cyber Security Professionals. Mastering tools associated with your profession will almost certainly make you more efficient and therefore productive.
In this post we will present an overview of “Five Popular Hacking Tools’ as voted by Cyber Security Professionals (such as Penetration Testers, Digital Forensics experts etc). This list was compiled from the Concise Courses Hacking Tools Directory.
“Hacker Tools”, the subject of this post, are typically placed within the following categories: Application Specific Scanners, Debuggers, Encryption Tools, Firewalls, Forensics, Fuzzers, Intrusion Detection Systems, Packet Crafting Tools, Packet Sniffers, Password Crackers, Port Scanners, Rootkit Detectors, Traffic Monitoring Tools, Vulnerability Exploitation Tools, Vulnerability Scanners, Web Browser Related, Web Proxies, Web Vulnerability Scanners and Wireless Tools.
It’s often said that “Guns don’t kill people; people kill people” – a saying that resonates somewhat with this subject matter since the tools listed below can be used to either assist with security auditing, or, sadly, for nefarious and criminal gain. Please exercise caution when experimenting with these tools; they should not be used to scan/profile/attack (“test”) web sites or networks that you do not own or have no legal authority to “test”.
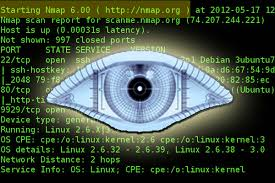
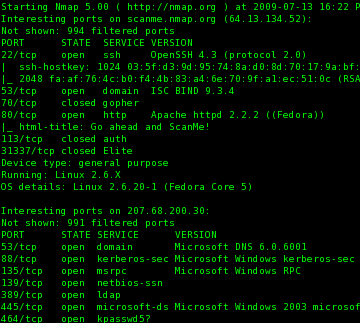
#1 Nmap
Featured on “The Girl with the Dragon Tattoo”, “Matrix Reloaded” and “Die Hard 4″, nmap is a hugely popular and useful port scanner that assists in finding computers on a network and finding out info all about them.
#2 Burp Suite
Burp Suite is an integrated platform for performing security testing of web apps, something which is central to our recently published title: How to Attack and Defend Your Websitefeatured all March long during Cybersecurity Month at Bluebottlebiz. Burp’s various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
#3 John The Ripper
Amongst other uses, John The Ripper (often abbreviated to simply ‘JTR’) is an expert ‘Brute Force” password cracker. We included this tool for those new to security since it will help you understand the mechanics of common password attacks such as “dictionary attacks”.
#4 Wapiti
We’ve included Wapiti because it has a real practical use: it helps the user to audit the security of web applications. Wapiti performs “black-box” scans, i.e. it does not study the source code of the application but will scans the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets this list, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
#5 The Social-Engineer Toolkit (SET)
Social Engineering is, in our opinion, an often overlooked subject in Cyber Security hence why we have included this tool. This Social-Engineer Toolkit was designed to perform advanced attacks against the human element. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
We’ve only just begun to scratch the surface with regards to the sheer quantity of tools out there in the wild, however, if you are new to the world of security then do go ahead and take a look at the above tools we’ve listed. For a more comprehensive list (including video tutorials) please visit Concise Courses.
Automated tools and the ability to remain anonymous are making it all to easy to execute cyber attacks. An understanding of how these tools work will help you firm your organization’s security posture.


1 comments On The Top Five Hacker Tools of 2015
Pingback: Сбор информации при пентестинге. - Cryptoworld ()